If you’re curious on how the OCSP stapling really works on your website, you come to a point that you do a lot of research before implementing in on your production. Let’s say you already have a testing website with the OCSP stapling enabled, the last thing you need to do is to verify if its working.
If you don’t know how to enable OCSP stapling in nginx, you can easily do that by using this command:
sudo certbot --nginx --must-staple -d yourwebsite -d www.yourwebsite.comAnd don’t forget to add a resolver (eg: resolver 1.1.1.1 1.0.0.1 8.8.8.8 8.8.4.4 208.67.222.222 208.67.220.220 valid=60s;) in your configuration to avoid getting this error:
no resolver defined to resolve ocsp.int-x3.letsencrypt.org while requesting certificate status, responder: ocsp.int-x3.letsencrypt.org, certificate: "/etc/letsencrypt/live/codefaq.org/fullchain.pem"How to Check OCSP Response Data
There are ways to check if your OCSP Stapling works properly, this is by using the querying from openssl command in your server’s SSH.
To do that, open up your SSH server: ssh -o ServerAliveInterval=30 root@your_server.com.
Then fire up this openssl command to view the “OSCP response data”.
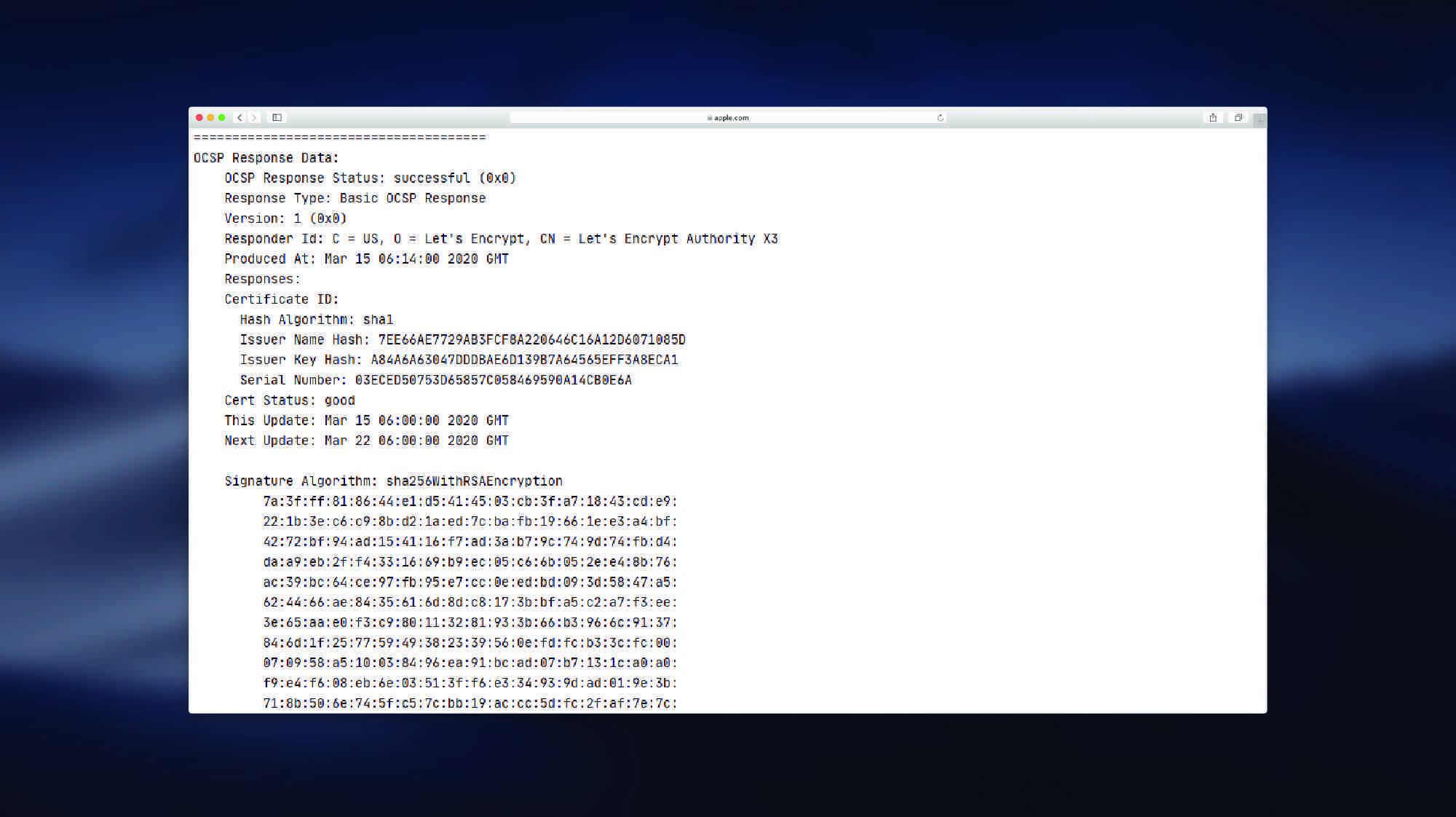
openssl s_client -connect codefaq.org:443 -status | awk -n '/OCSP response:/,/---/'You should see an example output below:
OCSP response:
======================================
OCSP Response Data:
OCSP Response Status: successful (0x0)
Response Type: Basic OCSP Response
Version: 1 (0x0)
Responder Id: C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3
Produced At: Mar 15 06:14:00 2020 GMT
Responses:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: 7EE66AE7729AB3FCF8A220646C16A12D6071085D
Issuer Key Hash: A84A6A63047DDDBAE6D139B7A64565EFF3A8ECA1
Serial Number: 03ECED50753D65857C058469590A14CB0E6A
Cert Status: good
This Update: Mar 15 06:00:00 2020 GMT
Next Update: Mar 22 06:00:00 2020 GMT
Signature Algorithm: sha256WithRSAEncryption
7a:3f:ff:81:86:44:e1:d5:41:45:03:cb:3f:a7:18:43:cd:e9:
22:1b:3e:c6:c9:8b:d2:1a:ed:7c:ba:fb:19:66:1e:e3:a4:bf:
42:72:bf:94:ad:15:41:16:f7:ad:3a:b7:9c:74:9d:74:fb:d4:
da:a9:eb:2f:f4:33:16:69:b9:ec:05:c6:6b:05:2e:e4:8b:76:
ac:39:bc:64:ce:97:fb:95:e7:cc:0e:ed:bd:09:3d:58:47:a5:
62:44:66:ae:84:35:61:6d:8d:c8:17:3b:bf:a5:c2:a7:f3:ee:
3e:65:aa:e0:f3:c9:80:11:32:81:93:3b:66:b3:96:6c:91:37:
84:6d:1f:25:77:59:49:38:23:39:56:0e:fd:fc:b3:3c:fc:00:
07:09:58:a5:10:03:84:96:ea:91:bc:ad:07:b7:13:1c:a0:a0:
f9:e4:f6:08:eb:6e:03:51:3f:f6:e3:34:93:9d:ad:01:9e:3b:
71:8b:50:6e:74:5f:c5:7c:bb:19:ac:cc:5d:fc:2f:af:7e:7c:
61:46:6a:04:aa:73:c1:92:b6:5e:81:71:34:d3:7e:08:84:87:
64:22:cc:c8:91:0d:7e:73:09:85:49:d6:e2:e8:a3:99:e0:90:
2d:93:aa:13:e6:ef:6c:ab:0a:49:0f:35:83:94:74:54:db:b0:
c2:e9:40:93
======================================
---This means your OCSP stapling works.